Security Options¶
Traffic Server provides a number of security features.
Controlling Client Access to the Proxy Cache¶
You can configure Traffic Server to allow only certain clients to use the proxy cache by editing a configuration file.
- Add a line in ip_allow.config for each IP address or range of IP addresses allowed to access Traffic Server.
- Run the command traffic_line -x to apply the configuration changes.
Configuring DNS Server Selection (Split DNS)¶
The Split DNS option enables you to configure Traffic Server to use multiple DNS servers, as dictated by your security requirements. For example, you might configure Traffic Server to use one set of DNS servers to resolve hostnames on your internal network, while allowing DNS servers outside the firewall to resolve hosts on the Internet. This maintains the security of your intranet, while continuing to provide direct access to sites outside your organization.
To configure Split DNS, you must do the following:
- Specify the rules for performing DNS server selection based on the destination domain, the destination host, or a URL regular expression.
- Enable the Split DNS option.
To do this, we
- Add rules to splitdns.config.
- In records.config set the variable proxy.config.dns.splitDNS.enabled to 1 to enable split DNS.
- Run the command traffic_line -x to apply the configuration changes.
Using SSL Termination¶
The Traffic Server SSL termination option enables you to secure connections in reverse proxy mode between a client and a Traffic Server and/or Traffic Server and an origin server.
The following sections describe how to enable and configure the SSL termination option.
- Enable and configure SSL termination for client/Traffic Server connections: Client and Traffic Server Connections
- Enable and configure SSL termination for Traffic Server/origin server connections: Traffic Server and Origin Server Connections
- Enable and configure SSL termination for both client/Traffic Server and Traffic Server/origin server connections: Client and Traffic Server Connections Traffic Server and Origin Server Connections, respectively.
Client and Traffic Server Connections¶
The figure below illustrates communication between a client and Traffic Server (and between Traffic Server and an origin server) when the SSL termination option is enabled & configured for client/Traffic Server connections only.
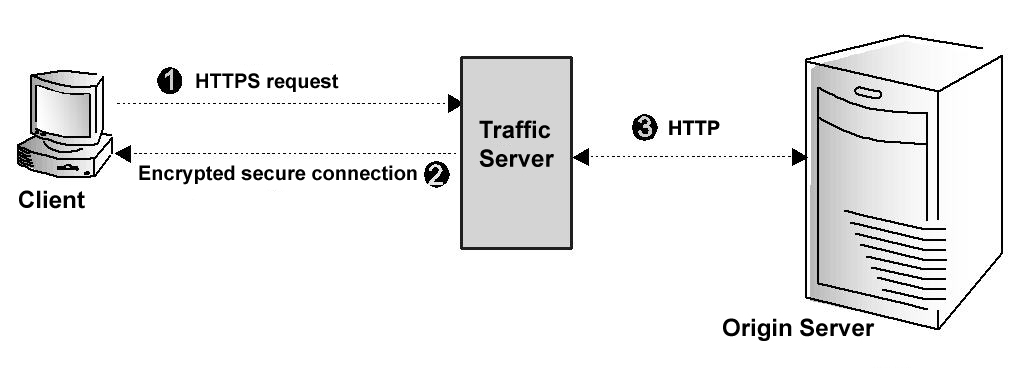
Client and Traffic Server communication using SSL termination
The figure above depicts the following:
- The client sends an HTTPS request for content. Traffic Server receives the request and performs the SSL ‘handshake’ to authenticate the client (depending on the authentication options configured) and determine the encryption method that will be used. If the client is allowed access, then Traffic Server checks its cache for the requested content.
- If the request is a cache hit and the content is fresh, then Traffic Server encrypts the content and sends it to the client. The client decrypts the content (using the method determined during the handshake) and displays it.
- If the request is a cache miss or cached content is stale, then Traffic Server communicates with the origin server via HTTP and obtains a plain text version of the content. Traffic Server saves the plain text version of the content in its cache, encrypts the content, and sends it to the client. The client decrypts and displays the content.
To configure Traffic Server to use the SSL termination option for client/Traffic Server connections, you must do the following:
- Obtain and install an SSL server certificate from a recognized certificate authority. The SSL server certificate contains information that enables the client to authenticate Traffic Server and exchange encryption keys.
- Configure SSL termination options:
- Set the port number used for SSL communication using proxy.config.http.server_ports.
- Edit ssl_multicert.config to specify the filename and location of the SSL certificates and private keys.
- (Optional) Configure the use of client certificates: Client certificates are located on the client. If you configure Traffic Server to require client certificates, then Traffic Server verifies the client certificate during the SSL handshake that authenticates the client. If you configure Traffic Server to not require client certificates, then access to Traffic Server is managed through other Traffic Server options that have been set (such as rules in ip_allow.config).
- (Optional) Configure the use of Certification Authorities (CAs). CAs add security by verifying the identity of the person requesting a certificate.
In order to accomplish this, we
- Edit the following variables in the SSL Termination section of records.config
- Run the command traffic_line -L to restart Traffic Server on the local node or traffic_line -M to restart Traffic Server on all the nodes in a cluster.
Traffic Server and Origin Server Connections¶
The figure below illustrates communication between Traffic Server and an origin server when the SSL termination option is enabled for Traffic Server/origin server connections.
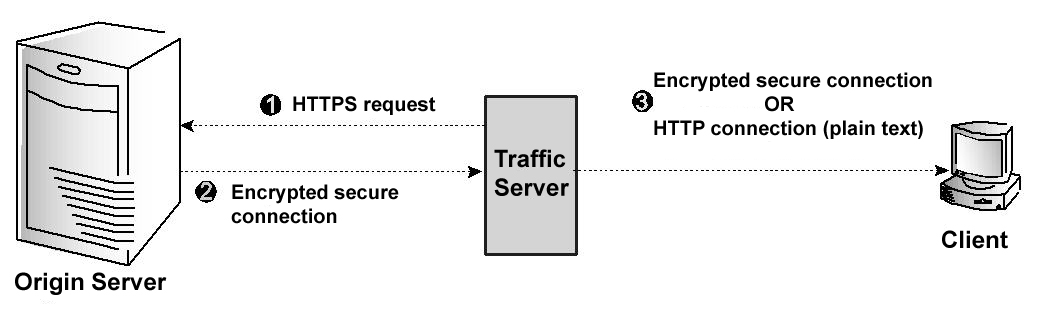
Traffic Server and origin server communication using SSL termination
The figure above depicts the following:
Step 1: If a client request is a cache miss or is stale, then Traffic Server sends an HTTPS request for the content to the origin server. The origin server receives the request and performs the SSL handshake to authenticate Traffic Server and determine the encryption method to be used.
Step 2: If Traffic Server is allowed access, then the origin server encrypts the content and sends it to Traffic Server, where it is decrypted (using the method determined during the handshake). A plain text version of the content is saved in the cache.
Step 3: If SSL termination is enabled for client /Traffic Server connections, then Traffic Server re-encrypts the content and sends it to the client via HTTPS, where it is decrypted and displayed. If SSL termination is not enabled for client/Traffic Server connections, then Traffic Server sends the plain text version of the content to the client via HTTP.
To configure Traffic Server to use the SSL termination option for Traffic Server and origin server connections, you must do the following:
- Obtain and install an SSL client certificate from a recognized certificate authority. The SSL client certificate contains information that allows the origin server to authenticate Traffic Server (the client certificate is optional).
- Configure SSL termination options:
- Enable the SSL termination option.
- Set the port number used for SSL communication.
- Specify the filename and location of the SSL client certificate (if you choose to use a client certificate).
- Specify the filename and location of the Traffic Server private key (if the private key is not located in the client certificate file). Traffic Server uses its private key during the SSL handshake to decrypt the session encryption keys. The private key must be stored and protected against theft.
- Configure the use of CAs. CAs allow the Traffic Server that’s acting as a client to verify the identity of the server with which it is communicating, thereby enabling exchange of encryption keys.
In order to accomplish this, we:
- Edit the following variables in the SSL Termination section of
records.config:
- proxy.config.http.server_ports
- proxy.config.ssl.client.verify.server
- proxy.config.ssl.client.cert.filename
- proxy.config.ssl.client.cert.path
- proxy.config.ssl.client.private_key.filename
- proxy.config.ssl.client.private_key.path
- proxy.config.ssl.client.CA.cert.filename
- proxy.config.ssl.client.CA.cert.path
- Run the command traffic_line -L to restart Traffic Server on the local node or traffic_line -M to restart Traffic Server on all the nodes in a cluster.